Validation Scripts
Real-time alerts, dashboards & structured search analysis
Establish best practices across your infrastructure
Free 30-day evaluation
Out-of-the-box security controls
Simplified compliance
Flexible Dashboards
Help you keep an eye on important metrics to ensure you stay up to date.
Reporting
Includes ready-to-run reports that can be scheduled, emailed or run on-demand.
Full SIEM
EventSentry includes log, FIM, AD & network traffic monitoring - in one single product.
Security
Alert on suspicious processes, malicious network activity, port scans and more.
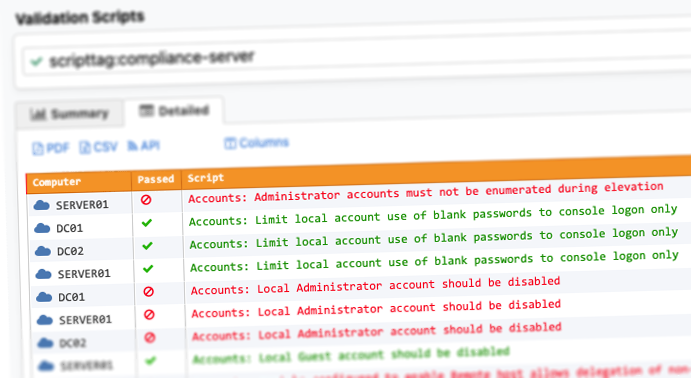
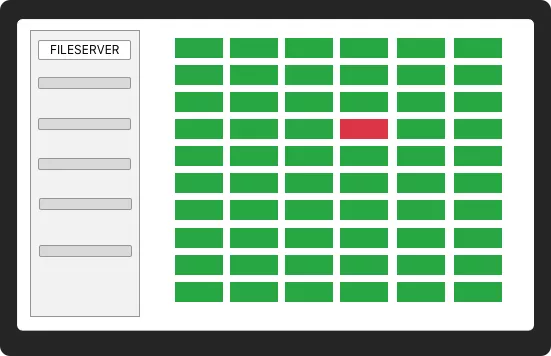
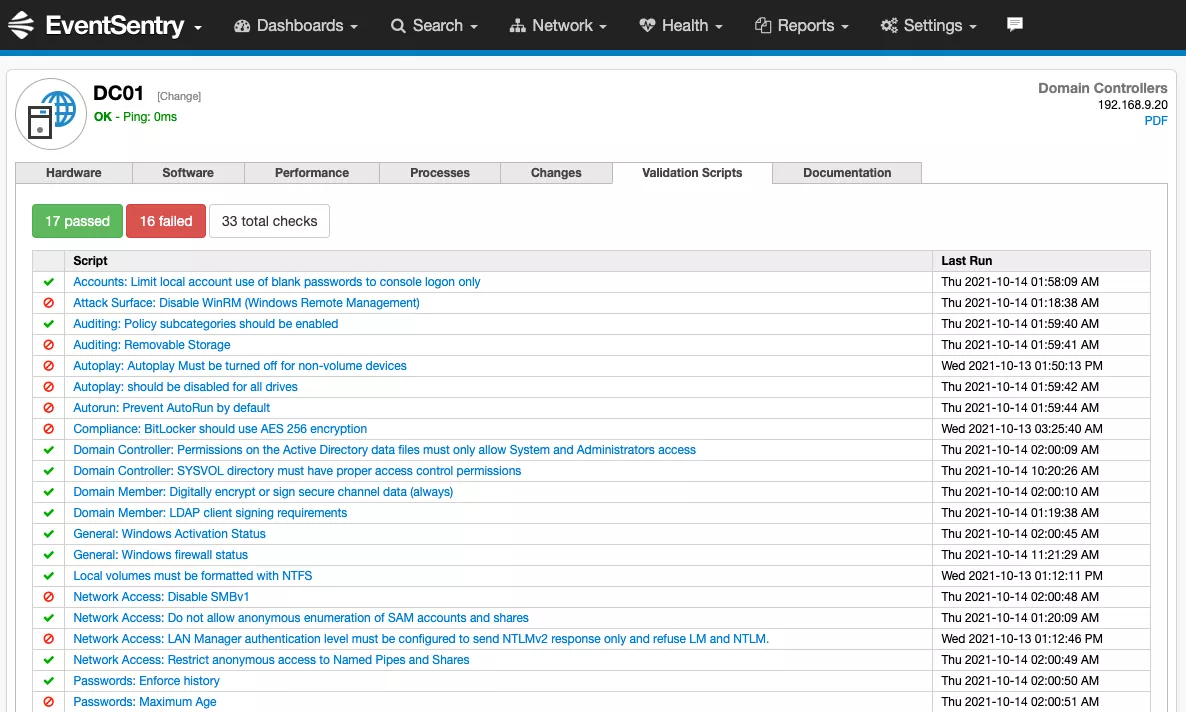
Validation
Validate security settings across your entire Windows network against required and recommended settings.
Health / Inventory
EventSentry also offers a complete software, hardware inventory along with health monitoring.
"In a day and age where everything has a maintenance agreement, this is one of the few that stand out as being genuinely worthwhile. The technician support is fantastic, the updates are regular and timely, and the product works like it is supposed to." >> READ MORE
Jamie H. (Director of IS&T, HIPAA Security Officer, PrimeWest Health)
"EventSentry’s multifaceted feature set has helped NMFTA predict and avoid Windows Server® crashes, Microsoft® SQL Server® failures, configuration problems in its VMware® environment, and malicious attacks against workstations and servers." >> READ MORE
Urban Jonson (CTO of NMFTA)
Perpetual License
You own the license
No Data Limit
Avoid unexpected costs
No Sensor Limit
Full visibility of your network
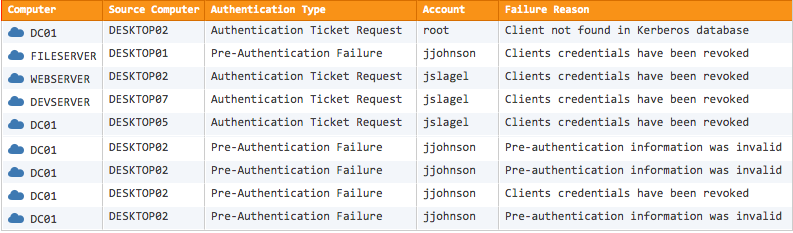
Normalized Security Events
EventSentry translates complex security events into easy to understand, actionable reports.
Affordable Event Log Monitoring Software
-
Start an evaluation
FREE fully functional for 30-days
-
Install EventSentry
Quick installation / Monitor in minutes
-
Monitor your infrastructure
Peace of mind included