Audit Failures pertaining to failed logon attempts are a common scenario on domain controllers in large networks, and setting up a filter to notify you when a user types in the wrong password will most likely result in hundreds of emails being sent to you.
In this example we will want to be notified if somebody types the wrong password more than 15 times during 10 minutes (or less).
To accomplish this, create an include filter that matches failed login attempts (e.g. Log=Security;Severity=Audit Failures;Event Source=Security;Event ID=675) and add the following threshold options to the filter. An explanation is giving below the screenshot.
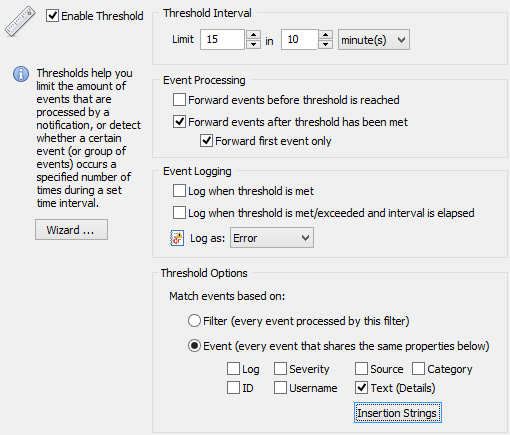
Event Processing: Forward events when/after threshold has been met
This option ensures that you are receiving events after the threshold of 15 has been met, however this could still result in many emails being sent if somebody is trying 100 different passwords. The option Forward first event only will make sure that you only receive the first event after the threshold has been met, that is the 16th event.
Match events based on: Text (Details)
The default option for thresholds is "Match events based on Filter", which means that the internal counter used by the threshold filter is increased every time an event matches the filter, even if it is from different user accounts. This is clearly not desirable in this case, as we want the filter to have a separate internal counter for each user.
This setting essentially tells the filter to keep/start a separate counter for each unique event text it counters. For this example an event text that is logged on the domain controller might look like this:
Pre-authentication failed:
User Name: myuser
User ID: MYDOMAIN\myuser
Service Name: krbtgt/NETIKUSNET
Pre-Authentication Type: 0x2
Failure Code: 0x18
Client Address: 192.150.3.20
It is also possible to filter this event on the workstation, in which case the event id would be 529 and the event text would look different:
Logon Failure:
Reason: Unknown user name or bad password
User Name: myuser
Domain: MYDOMAIN
Logon Type: 7
Logon Process: User32
Authentication Package: Negotiate
Workstation Name: WORKSTATION1
It might be tempting to click the Username checkbox instead of the Text (Details) checkbox, however this would not work since all events are logged by the NT AUTHORITY\SYSTEM user account.
|
Event logs should be investigated immediately using the web reports on event viewer when EventSentry notifies you of many failed login attempts so that corrective action (e.g. temporarily disable the user) can be taken. |
