Sysmon, a free utility that is part of the Microsoft Sysinternals Suite, enhances the built-in process auditing capabilities of Windows by providing additional details about processes, most importantly network activity. Analyzing all network activity of processes can help detect Malware and other threats in real time as well as aid with forensic analysis.
Since Sysmon is a free utility and can be automatically installed with EventSentry, it is recommended to deploy Sysmon to all monitored hosts and capture relevant events from Sysmon. The type of information that Sysmon captures is configurable, and the configuration template provided by SwiftOnSecurity (see below) is a good starting point.
To install Sysmon using the SwiftOnSecurity template, follow the steps below:
•Download Sysmon and extract the executables into a temporary folder
•Download the SwiftOnSecurity template from https://github.com/SwiftOnSecurity/sysmon-config and store it in the same directory as sysmon
•Run sysmon64.exe -accepteula -i sysmonconfig-export.xml
•Monitor the Microsoft-Windows-Sysmon/Operational event log
•Setup alerts (optional)
|
Built-In event log filters that can identify malicious activity based on Sysmon events are available here. |
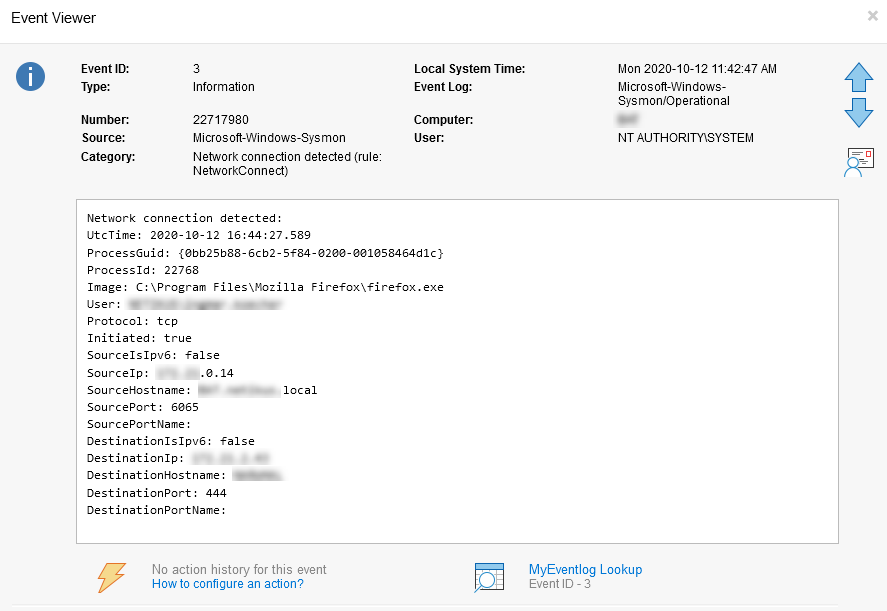
Sysmon event showing a network connection initiated by Firefox
