You can specify which types of file access are being tracked to ensure that only relevant events are being recorded in the database. Additionally, you can setup file filters to include or exclude files that match a pattern.
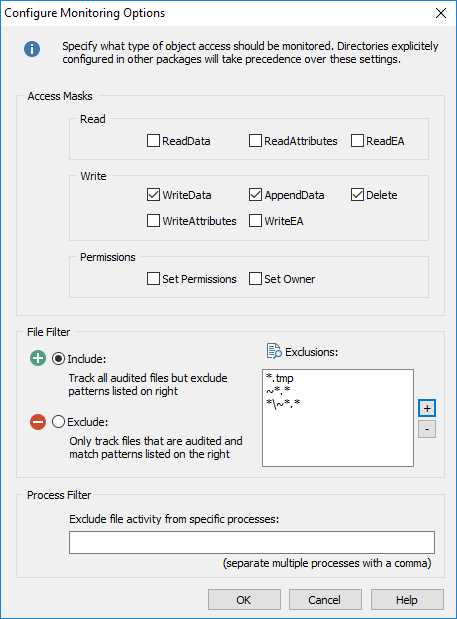
Access Masks
Windows distinguishes between the following access masks when recording file access activity, either through regular or operational events:
•ReadData •ReadAttributes •ReadEA
•SetPermissions •SetOwner |
•WriteData •WriteAttributes •WriteEA •AppendData •Delete |
For example, to track when users change files, make sure that WriteData and AppendData are both selected. To record when files are deleted, make sure that Delete is checked.
File Filter
The default filter ("Include") includes all files but lets you specify exclusion on a by case basis. For example, you could exclude all files that have a tmp extension by specifying the following filter:
*.tmp
|
File names and paths need to be specified relative to the monitored folder. For example, if you are monitoring the folder C:\Logfiles, but want to exclude any file in the Temp sub directory (C:\Logfiles\Temp), then you would need to specify the filter as Temp\*.*. |
Process Filter
File activity triggered by specific processes can be excluded from being tracked with the process filter. Specify either the full path to the process or use a wildcard character, for example:
*filescanner.exe
C:\Program Files\FileScannerSoftware\filescanner.exe
Multiple processes can be separated with commas.
|
Excluding a process only works if the process in question directly accesses the files (and not via a network share) and is listed on the 4663 events. As such, processes running on clients accessing remote files cannot be excluded, since the server/host accessing the files is not aware of those (remote) processes. |
