Intercepts Windows audit events pertaining to the Windows Registry and makes them available in the web-based reporting.
|
Requirements: This feature works by intercepting Audit Success events with event ID 4657 that are written to the security event log when registry auditing is enabled (either in the local security policy or via AD) and at least one registry key is configured for auditing. See requirements for details. |
Collected Data
The following registry information is collected on all supported Windows platforms:
Field |
Description |
Action |
Added, Removed or Modified |
Registry Path |
Path of the value that was added, removed or modified, always starts with \REGISTRY\ |
Registry Value Name |
Name of the registry value that was added, removed or modified |
Value Before |
Value before the change |
Value After |
Value after the change |
Type Before |
Type of the value before the change |
Type After |
Type of the value after the change |
Caller Path / File |
Proesses that initiated the change, ignore for changes that were initiated removely |
Username |
User who initiated the change |
Logon ID |
Logon ID of the session that made the change |
Event # |
Event number of the event describing the change |
Configuration
General Filter
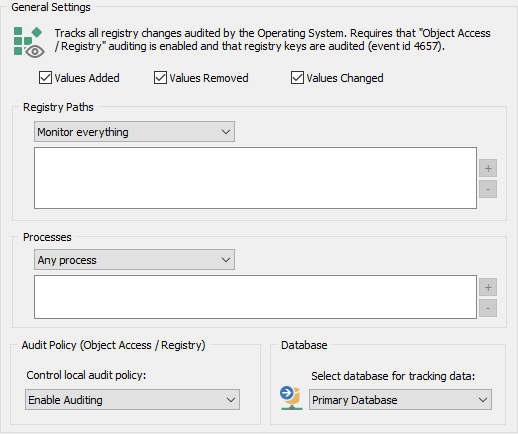
Determines which registry activity will be picked up.
Registry Paths
Configure whether all registry changes that are audited by the Operating System are processed by EventSentry (Monitor everything), whether certain paths should be excluded ("Exclude paths listed below") or whether only select paths should be monitored ("Monitor only paths listed below").
Registry path filters need to match the format used in event 4657 and generally start with \REGISTRY\, for example:
\REGISTRY\MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
\REGISTRY\USER\S-1-5-21-2574282233-618468577-1958264051-1122\Software\Microsoft\Windows\CurrentVersion\Run
When in doubt prefix the registry path with an asterisk, for example *\Software\Microsoft\Windows\CurrentVersion\Run
Sub folders are automatically monitored.
Processes
Configure whether registry activity from all processes should be processed ("Any process"), whether certain processes should be excluded ("Exclude Processes listed below") or whether only specific processes should be monitored ("Monitor only processes listed below").
Event IDs |
Registry Access
4657, 4663 |

