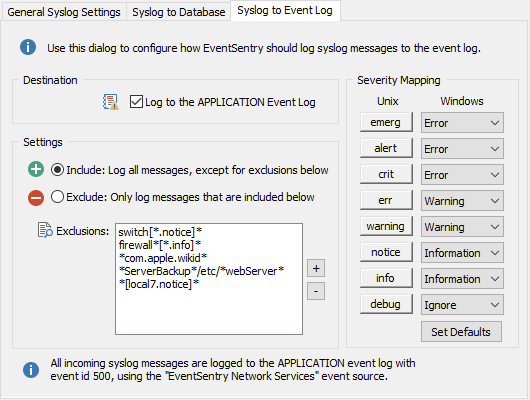
Incoming Syslog packets can be logged to event log to facilitate real-time alerts, e.g. via email. The feature is enabled on the "Syslog to Event Log" tab with the "Log to the APPLICATION event log" check box. Since the Syslog protocol supports 8 different severities (compared to just 3 for the Windows event log), a mapping of severities needs to be configured.
EventSentry will log all messages to the application event log with event ID 500 and event source EventSentry Network Services.
Severity Mapping
Configures the mapping between Syslog severities and Windows event log severities.
Unix Syslog defines eight severity levels:
•EMERG Emergency •ALERT Alert •CRIT Critical •ERR Error •WARNING Warning •NOTICE Notice •INFO Info •DEBUG Debug
The Windows event log defines only three severities (SUCCESS is not mentioned since it is basically equivalent to INFORMATION):
•ERROR •WARNING •INFORMATION •Ignore (does not log message to the event log) |
|
|
To prevent a certain error level (e.g. debug) from being written to the Windows event log, specify Ignore in the corresponding Windows column. This will drop all packets from the specified error level without logging them to the event log. |
Settings
By default, no incoming Syslog messages will be logged to the event log. Clicking the + icon will add additional filters to the list (see below for filtering syntax and examples). Wildcards * and ? are supported.
Include: Log all messages to the event log, except for exclusions below
This setting will log all Syslog messages to the event log. Syslog messages containing strings that are listed below will be excluded.
Exclude: Only log messages to the database that are included below
This is the default setting, and only logs Syslog messages to the event log that match the listed filters.
Syntax
Syslog message filters are compared to the following Syslog format:
hostname[facility.severity]: content
ipaddress[facility.severity]: content
hostname: The host name of the remote host, if the remote IP address as was able to be resolved to a host name
ipaddress: The IP address of the remote host, if the host name could not be resolved with a reverse lookup
facility: The Syslog facility, e.g. auth, cron, kern, etc.
severity: The Syslog severity, e.g. emerg, alert, crit, etc.
content: The actual content of the Syslog message
Examples:
firewall01.prod.local[kern.crit]: Invalid login from 11.32.23.111
192.1.3.4[cron.notice]: /USR/SBIN/CRON[26051]: (root) CMD ( cd / && run-parts --report /etc/cron.hourly)
ubuntu-box[authpriv.notice]: sudo: root : TTY=unknown ; PWD=/ ; USER=administrator ; COMMAND=/usr/bin/gconftool --get /system/http_proxy/use_http_proxy
Example Filters
•Match all "info" severities from hosts that start with "firewall": firewall*[*.info]*
•Match all messages that contain "com.apple.wikid": *com.apple.wikid*
•Match all messages from facility "local7" with severity "notice": *[local7.notice]*
•Match all messages from hosts from the 192.1.1.0/24 subnet: 192.1.1.*