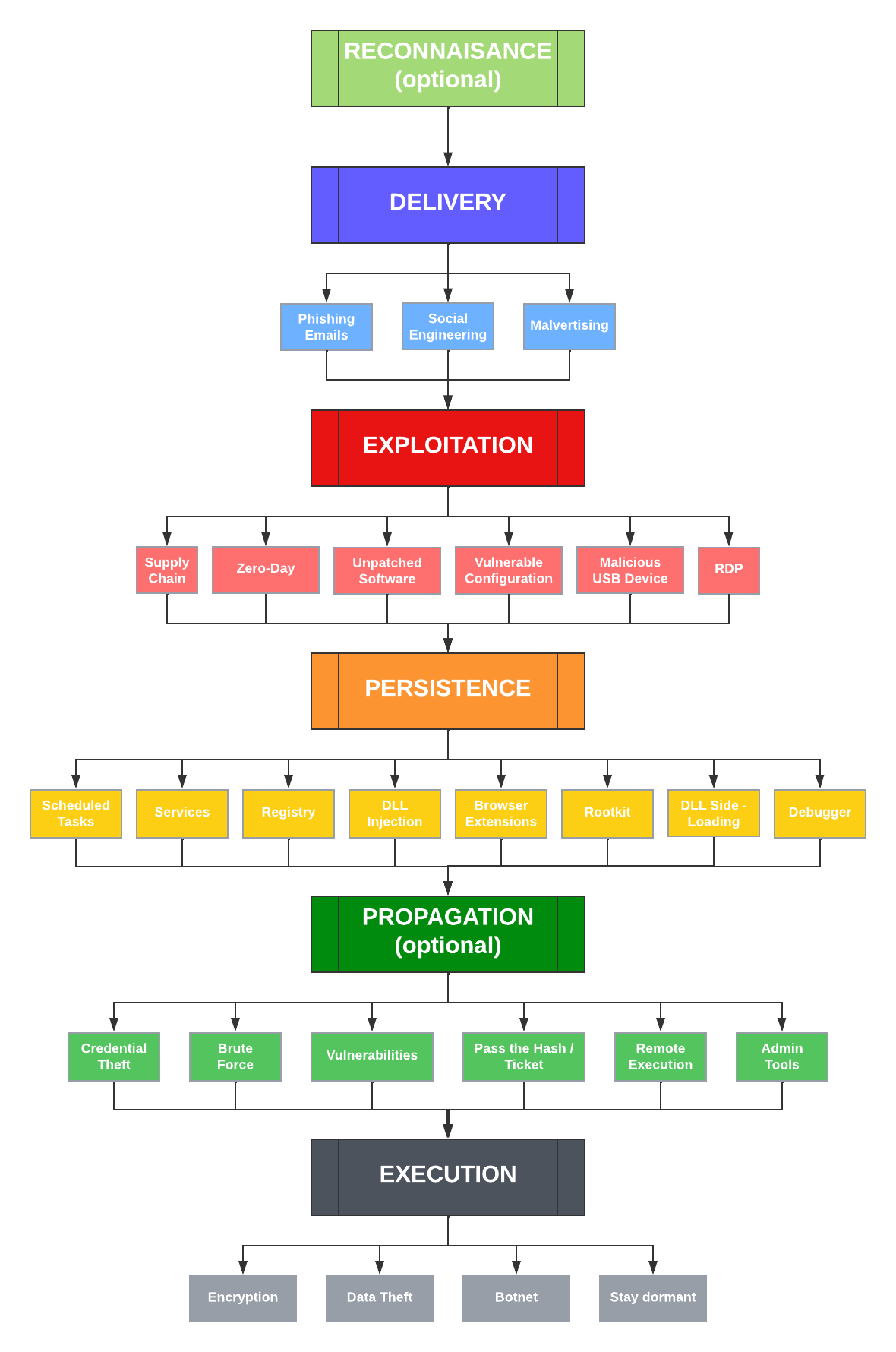
Malware poses an ongoing and growing challenge to governments, institutions, businesses and private individuals.
This guide offers insight into common practices and methods employed by threats of all kinds, including Malware & Ransomware.
EventSentry's real-time monitoring and detection features can help both prevent and detect many of these threats, which is are key to minimizing damage, preventing data loss and maintaining business continuity.
EventSentry detection methods are agnostic to specific types of malware, and accomplishes detection by monitoring hosts and networks from multiple vantage points.
1.Real-Time Log Monitoring
- Anomaly Detection
- Advanced Log Correlation (chains, timers, thresholds, ...)
- File Integrity Monitoring (FIM)
2.Ongoing Security Analysis
- Validation Scripts
- Active Directory Inventory
- Audit Policy Monitoring
3.Inventory Monitoring
- Scheduled Tasks
- Services & Drivers
- Browser Extensions
- Permissions
- Software & Windows Patches
- USB storage Devices
4.Active Directory
- User, Group & Computer Inventory
- Object Monitoring
- Group Policy Monitoring
5.Real-Time Security Dashboards
6.Extensive Data Collection for Forensics
7.Enhanced Audit Reporting
- Process Activity (incl. Sysmon)
- Network Logon Activity (incl. RDP)
- File Access Activity
8.Network Traffic Analysis
- Observe traffic to/from malicious IPs
- Detect new hardware devices
While EventSentry (and other security products) may not detect every activity by malware, it's wide array of monitoring features usually flag at least one type of activity performed by Malware. It is however still essential to protect networks from multiple angles to reduce the attack surface in the first place, including:
•User Education & Awareness
- Mitigates social engineering and phishing attacks
•Email Security
- Mitigates phishing attacks
•Firewalls & Perimeter Security
- Reduces attack surface
•Patch Management
- Mitigates software and OS vulnerabilities
•Antivirus Software
| - Detects infections and known threats |