Network logon tracking collects a wide variety of information about successful and failed logins on a network. Network logon tracking is useful in a variety of scenarios:
•Regulatory Compliance
•Network Security Review
•Troubleshooting
•Network Logon Statistics
For example, the following statistics / reports can be created with the data gathered:
•Most common reasons for failed logons
•Servers / Workstations with most failed logons
•Most common logon types (e.g. service, interactive, etc.)
•Protocol distribution (e.g. NTLM vs. Kerberos)
•and much more
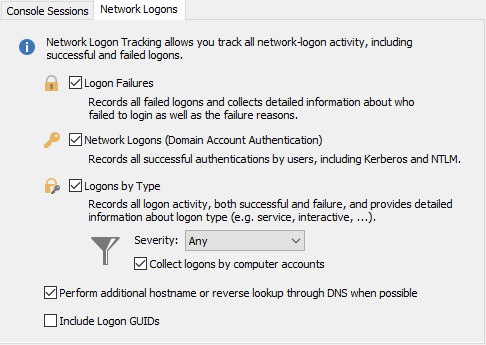
Logon Failures
Documents all authentications to domain controllers by users. Note that whenever such a user logs onto their own workstation or member server, this will generate a Network logon to a DC since the user’s workstation must access the domain controller under the user’s credentials to apply Group Policy / User Configuration.
Network Logons
Documents all authentications to domain controllers by users. Note that whenever such a user logs onto their own workstation or member server, this will generate a Network logon to a DC since the user’s workstation must access the domain controller under the user’s credentials to apply Group Policy / User Configuration.
Logons By Type
Documents all logons to monitored servers. It provides the following:
•Complete record of all attempts to access the computer, regardless of the type of account used
•Type of logon and logon process
•IP address and name of the client computer
Filter Events by Severity
Due to the high volume of events generated by Windows, this feature may record a large number of events. You can set the "Severity" option to "Audit Failures Only" to reduce the number of events that are captured by this feature. If you are required by law to capture this data, then verify with your compliance officer (and/or audit requirements) to ensure that you can change this setting and still remain compliant.
Collect Logons by Computer Accounts
Network logons by computer accounts can account for a large number of records in the database and dilute reporting. Uncheck the box to ignore any audit events which originate from computer accounts.
Perform additional host name or reverse lookup through DNS
When the logon id contained in the logon event (only applies to audit success events) can be linked (correlated) to an earlier logon session, then EventSentry will include the IP address and/or host name. In the case that only the host name or IP address are available, a DNS (reverse) lookup will be performed to gather the missing information.
Due to the nature of DNS lookups, this information might not 100% accurate and should not be solely relied upon.
Logon GUIDs
Captures the logon GUID available in some logon events and includes it in the search results. Capturing Logon GUIDs is generally not necessary as it provides little benefit for forensic analysis but can significantly degrade the performance of the collector in networks that generate a lot of logon GUIDs in a short amount of time.
