The System Monitor service & driver (Sysmon in short) logs a variety of events - mostly in response to process activity that occurs on a system - to the Microsoft-Windows-Sysmon/Operational event log. Sysmon events are similar to the 4688 and 4689 events logged by Windows to the security event log when a process starts and exits, the events generated by Sysmon are significantly more detailed however and cover other areas such as network activity, file write activity and more.
When configured to log network activity, Sysmon will log an event whenever a Windows process creates a network connection:
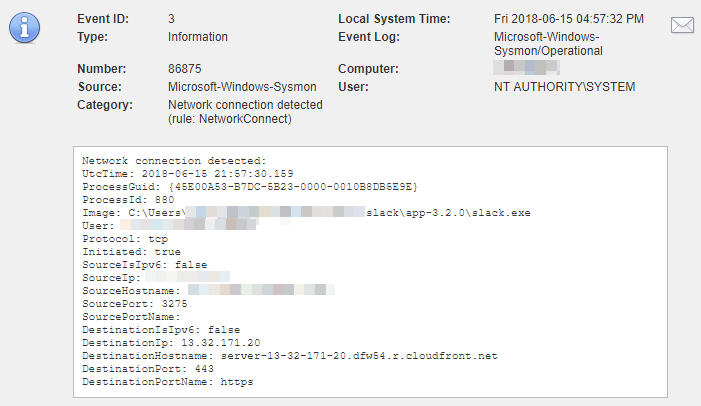
Sysmon logs network activity by slack.exe
When enabled, EventSentry intercepts event id 3 from the Microsoft-Windows-Sysmon/Operational event log which indicates that a local process created a network connection. This data is correlated to process tracking data collected from the Windows security event log and available in the web reports. If Sysmon data is available for a process tracking entry, then a black plus icon will be shown next to the PID in the web reports.
If EventSentry is configured to also collect NetFlow data, the data provided by Sysmon can be used to examine the associated network traffic generated by the process. Every row in the Sysmon report provides a link to the NetFlow History report.
Sysmon Installation
Sysmon can be downloaded from https://docs.microsoft.com/en-us/sysinternals/downloads/sysmon#configuration-files and installed from an elevated command prompt with one of the following two commands:
Default install with network connections |
Install with custom Sysmon configuration file (additional logging) |
Sysmon64.exe -accepteula -i -n |
Sysmon64.exe -accepteula -i "C:\Program Files\EventSentry\resources\sysmon.conf" |
The -n switch is important as it instructs Sysmon to log network activity from processes. Substitute "Sysmon64.exe" with "Sysmon.exe" on 32-bit systems. Despite of what is stated in the official documentation, a reboot is often necessary to activate the logging of event id 3.
To verify that Sysmon was installed and configured correctly, run sysmon64 -c which should yield output similar to what is shown below (when installed with -n option)
System Monitor v7.03 - System activity monitor
Copyright (C) 2014-2018 Mark Russinovich and Thomas Garnier
Sysinternals - www.sysinternals.com
Current configuration:
- Service name: Sysmon64
- Driver name: SysmonDrv
- HashingAlgorithms: SHA1
- Network connection: enabled
- Image loading: disabled
- CRL checking: disabled
- Process Access: disabled
It is important that Network connection is set to enabled.
|
NETIKUS.NET ltd and EventSentry are not affiliated with Sysinternals in any way and are unable to provide support for the Sysmon utility. |
