To log NetFlow data to the event log, click the "NetFlow to Event Log" tab, check the "Log to the APPLICATION Event Log" check box and specify the severity under which NetFlow data should be logged. To avoid flooding the Application event log with NetFlow-related alerts, the frequency of NetFlow alerts can be limited.
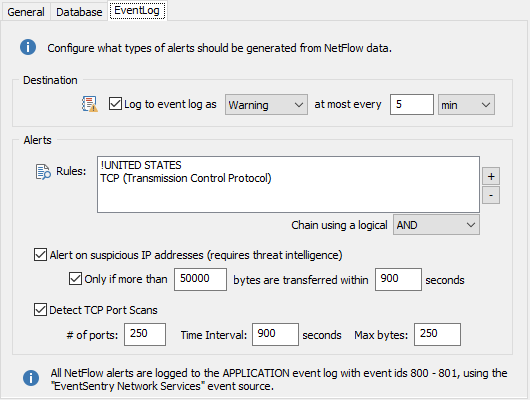
Alert Logic
Contains the rules under which NetFlow traffic information is logged to the event log. Rules can evaluate based on:
•The protocol
•The IP address
•Geolocation (country, state, city, zip code)
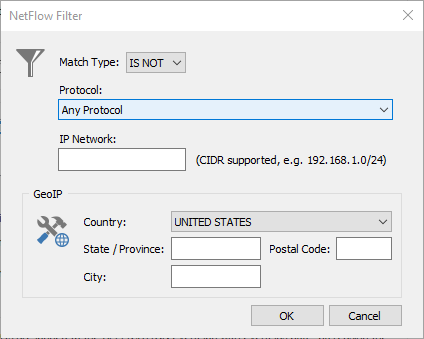
Multiple rules can be combined using either AND or OR logical operators. Individual rule entries can be negated by selecting the "IS NOT" match type (see below).
Alert on suspicious IP addresses
Logs event 820 (EventSentry Network Services / NetFlow) to the event log if a suspicious IP address has been encountered. The alert includes the source and destination IP address, affected port, threat count and threat details.
Only if more than ...
Logs event 830 (EventSentry Network Services / NetFlow) when more than the specified number of bytes are transferred to/from a suspicious IP address within the specified time interval. This can potentially detect irregular network activity such as APTs and also help reduce potential false alarms. Enabling this feature will no longer log event id 820.
Detect TCP Port Scans
Logs event 801 (EventSentry Network Services / NetFlow) to the event log if a potential port scan was detected:
# of ports: The number of different ports a remote host has to attempt to connect to in order to trigger an alert (default is 250)
Time Interval: The time interval (in seconds) during which the port scan has to occur (default are 900 seconds)
Max Bytes: Network packets will need to be smaller or equal than this size to be considered part of a potential port scan (default is 250)