How to get an email alert if a user attempts to log on more than X times with a wrong password?
Article ID: 407
Category: Compliance
Updated: 2019-09-12
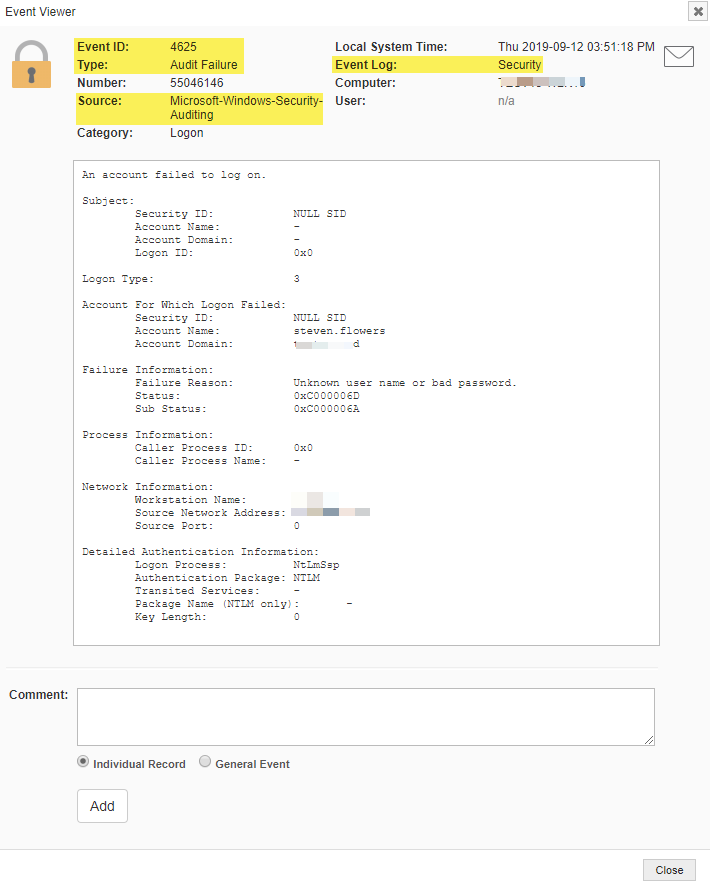
The easiest way to get notified in real-time whenever a user attempts to log on more than X times with a wrong password is by forwarding “Microsoft-Windows-Security-Auditing” event 4625. This event is logged to the Security event log whenever a user fails to logon.
More information on event id 4625, including associated audit settings, is available on system32.eventsentry.com
- Open the management console and either find an existing event log package to add this new filter rule to, or create a new event log package.
- Make sure the package is assigned to individual servers or make it global so that it applies to all hosts in your environment.
- Create a new event log filter that matches the following properties:
Event Log: Security Severity: Audit Failure Source: Microsoft-Windows-Security-Auditing Category: Logon Event ID: 4625 - Click "Threshold" and enable "Agent-Side" from the drop-down.
- Set a threshold that is appropriate for your environment, e.g. 3 in 1 minute. You can tweak this value later.
- Click "Forward After the threshold has been met" & "Forward first event only" in Event Processing.
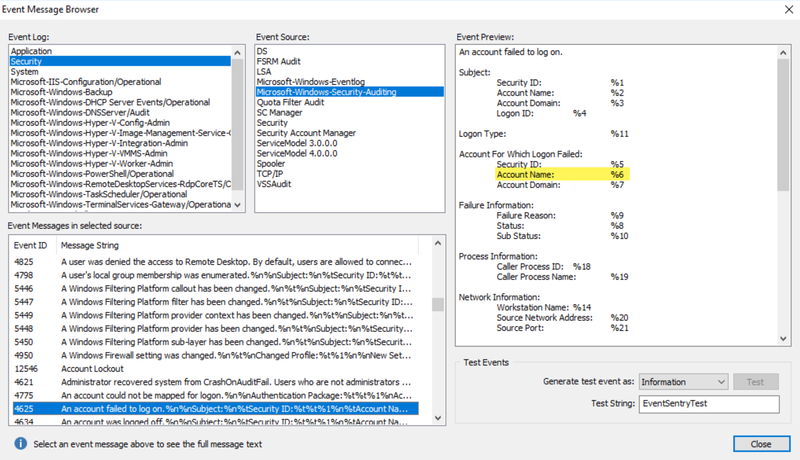
- Check the "Event Properties" radio button and then click "Insertion Strings" then number "6" from the drop-down and then "+" and "OK".
NOTE: The insertion string 6 represents the account name of the user that failed to login, setting the filter this way means that the same user will have to fail to log in X number of times in X minutes