Detecting and automatically recovering from bypassing Windows logons with utilman.exe
Utilman.exe is the utility program that is launched when the "Ease of Access" button on the login screen is clicked. At the time of writing, it is still vulnerable to be replaced by cmd.exe, allowing an attacker to simply reset any user password since the tool is executed with admin rights (Info).
This guide will illustrate how to monitor utilman.exe and, when a change to this file is detected, execute an embedded script to perform a number of tasks to alleviate the threat:
- Block access to the file (this includes delete, rename, and execution)
- Change the user password
- Turn off the computer
Performing these actions will make it more difficult for the attacker to use this exploit. This action can be replaced with other actions as desired. At the same time an email alert will also be sent.
- Creating an embedded script.
- Creating an Action pointing to the embedded script
- Creating Event Log filter
- Assign the filter to machines
Creating an Embedded Script
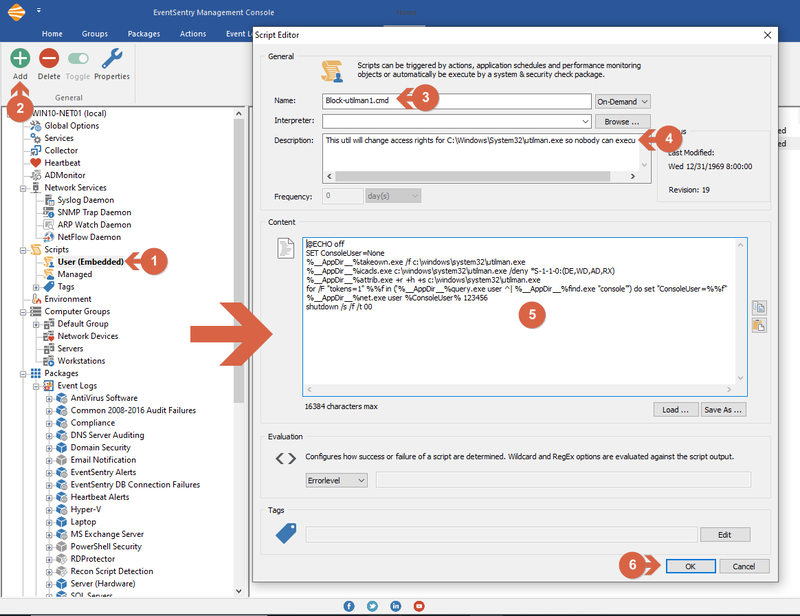
To create an embedded script, (1) left click "User (embedded)" under "Scripts" then (2) "Add" from the ribbon. (3) Enter the desired script name ending with .cmd (since this will be a windows batch script), (4) a description and (5) content. In EventSentry v4.1 and earlier, embedded scripts are managed via Tools -> Embedded Scripts. The contents of the script are below:
@ECHO off
SET ConsoleUser=None
%__AppDir__%takeown.exe /f c:\windows\system32\utilman.exe
%__AppDir__%icacls.exe c:\windows\system32\utilman.exe /deny *S-1-1-0:(DE,WD,AD,RX)
%__AppDir__%attrib.exe +r +h +s c:\windows\system32\utilman.exe
for /F "tokens=1" %%f in ('%__AppDir__%query.exe user ^| %__AppDir__%find.exe "console"') do set "ConsoleUser=%%f"
%__AppDir__%net.exe user %ConsoleUser% 123456
shutdown /s /f /t 00
Note: full path of commands added for security
Creating an embedded script
Creating an action pointing to the embedded script
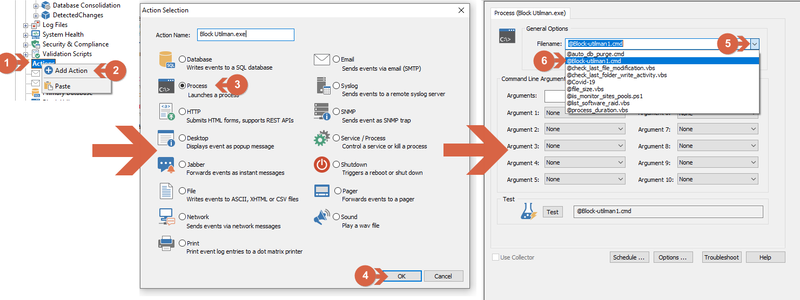
An action must be created that points to the just created embedded script. (1) Right-click over Actions and select (2) Add Action. From the Action window, select (3) process, and (4) click ok. From the process action window, (5) select the previously created embedded script from the file name list (6).
Creating an action pointing to the embedded script
Creating Event Log Filter
EventSentry already includes a pre-shipped package that will detect and alert when files inside the System32 window folder are deleted/added/modified (Packages/System Health/File Monitoring System32 32/64 Bits). As such, a filter must be created to trigger the action when the file utilman.exe is modified.
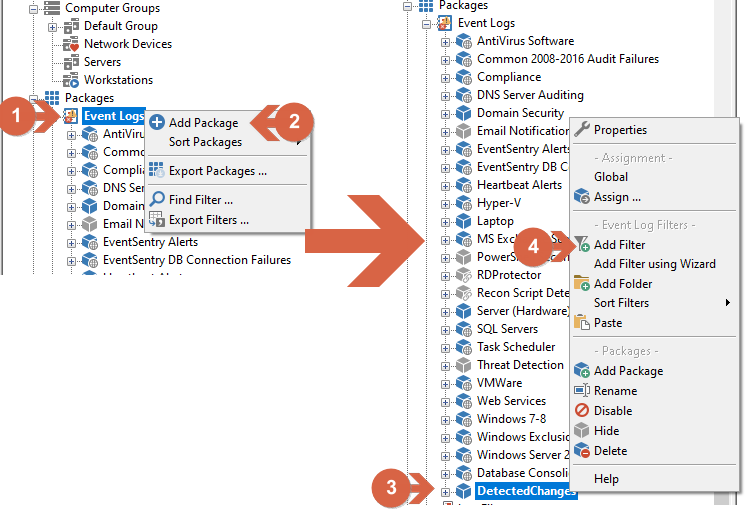
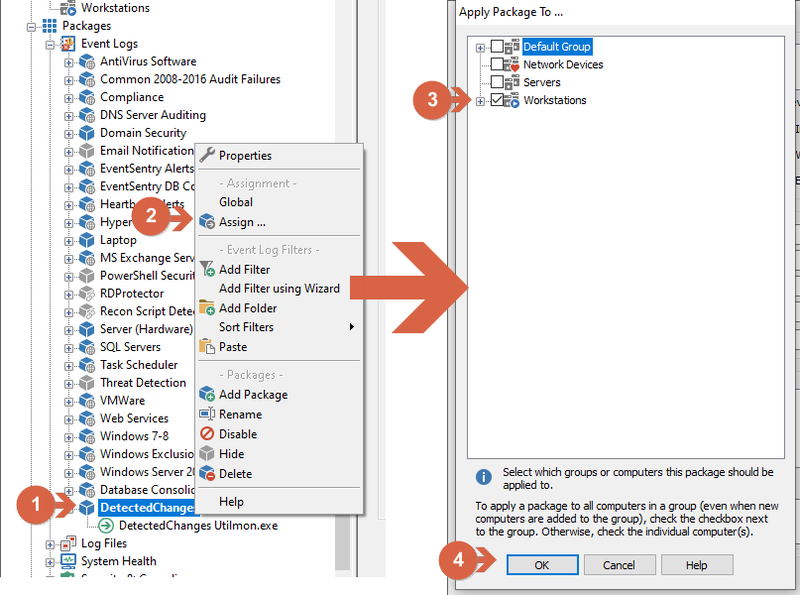
(1) Right-Click Event Logs under the Packages menu, (2) click on Add Package, (3) enter the package name (DetectedChanges used for this example), right-click it and (4) click Add Filter.
Creating an Event Log filter
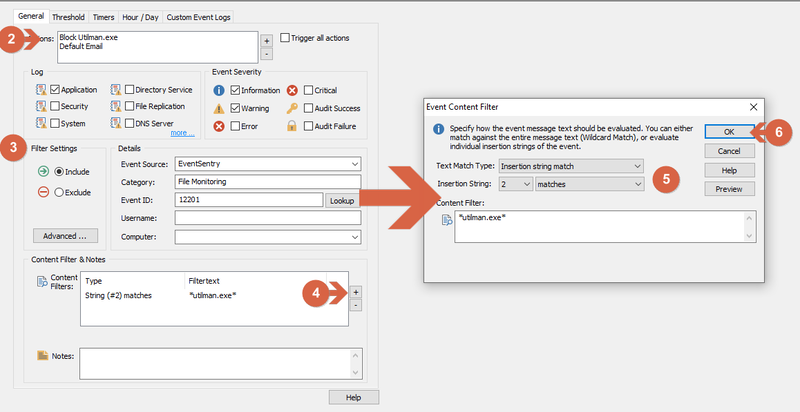
- Specify the filter name (Detected Changes Utilman.exe used for this example)
- In the filter window, add the just created action (Block Utilman.exe) and Default Email.
- Filter options:
Log: Application
Event Severity: Information and Warning
Filter Settings: Include
Event Source: EventSentry
Category File Monitoring
Event ID: 12201 - Under Content Filter & Notes click the "+" button.
- At event Content Filter windows, text match type should be insertion string match, insertion string: 2 Matches and enter utilman.exe
- Click OK.
Configuring an Event Log filter
Assign the filter to machines
Assign the filter to machine or group of machines by (1) right-clicking over the just created package, (2) clicking on Assign, (3) selecting a machine or group (4) and clicking OK.
Assigning a package
Always remember to save the configuration by clicking Home and Save.
Attack Simulation