Monitoring process CPU usage on Linux hosts
While overall performance and CPU statistics from non-Windows hosts can easily be obtained via SNMP, getting the CPU usage of each process requires a few additional configuration steps.
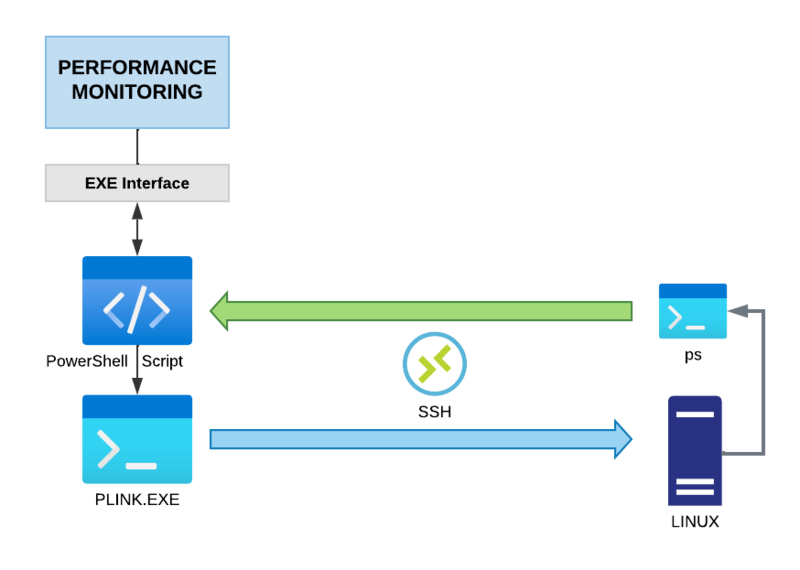
Since EventSentry's performance monitoring feature supports importing data returned from an external process (example), data returned from any process or script can be utilized for performance monitoring.
The plink.exe utility (part of PuTTY) supports executing processes on a remote Linux host (similar to psexec on Windows) and displaying its output locally (on the Windows host where EventSentry is installed).
PowerShell can then be utilized to parse the data so that it can be formatted for EventSentry's performance monitoring. The PS script below calls plink.exe, using a certificate login, to issue a ps command that lists every process and its CPU usage.
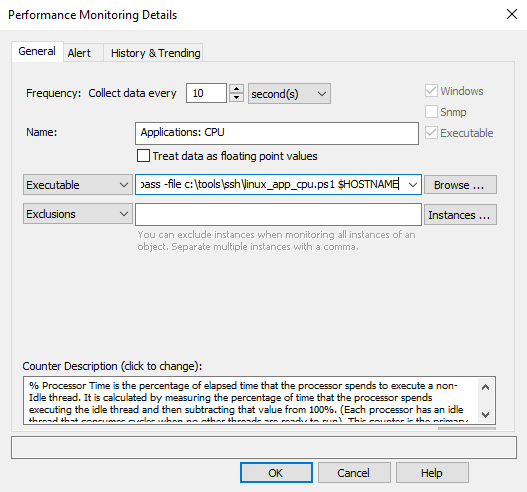
The script es_linux_process_cpu.ps1 can be downloaded and referenced in the "Executable" field of a performance object in a system health package (Packages - System Health - Performance Applications - Applications: CPU. Since the script is executed by the EventSentry Heartbeat Monitor service, the $HOSTNAME or $IPADDRESS variable need to be passed so that the script can be used universally.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 |
If ($args.Length -le 0)
{
Write-Host "Hostname argument required"
Exit(1)
}
# Path to the plink utility
$pathToPlink = "c:\tools\ssh\plink.exe"
# User for SSH login
$sshUser = "sshUser"
# Path to SSH public key cert, user/pass auth can be used an alternative, can also be customized to use cmd arg
$sshPathToCert = "C:\tools\ssh\sshCert"
$procInstance = @{}
$pinfo = New-Object System.Diagnostics.ProcessStartInfo
$pinfo.Arguments = '-batch -i ' + $sshPathToCert + ' -l ' + $sshUser + ' ' + $args[0] + ' "ps -eo %cpu,cmd"'
$pinfo.FileName = $pathToPlink
$pinfo.RedirectStandardError = $true
$pinfo.RedirectStandardOutput = $true
$pinfo.UseShellExecute = $false
$pinfo.CreateNoWindow = $true
$p = New-Object System.Diagnostics.Process
$p.StartInfo = $pinfo
$p.Start() | Out-Null
$stdout = $p.StandardOutput.ReadToEnd()
$stderr = $p.StandardError.ReadToEnd()
$processes = @()
$cpuValues = @()
$lines = $stdout.Split("`n")
ForEach ($line in $lines)
{
$tokens = $line.Split(" ")
If ($tokens.Count -gt 2)
{
$cpuUsage = $tokens[1]
$processName = $tokens[2]
try
{
$cpuValues += [Math]::Round($cpuUsage)
$processName = $processName.TrimEnd(":")
$processName = $processName.TrimEnd(")")
$processName = $processName.TrimStart("-")
$processName = $processName.TrimStart("(")
$processNameOutput = $processName
If ($procInstance[$processName] -gt 0)
{
$processNameOutput += "#"
$processNameOutput += $procInstance[$processName]
}
$processes += $processNameOutput
If ($procInstance[$processName] -eq '')
{ $procInstance[$processName] = 1 }
Else
{ $procInstance[$processName]++ }
}
catch {
}
}
}
$processes -join ","
$cpuValues -join ","
|