Automatically monitoring Microsoft Office Documents for threats
EventSentry can integrate with Decalage's oletools to scan Microsoft Office files on your hosts for threats. This is useful, for example, if you have a file server where you would like to monitor all newly added Office documents and scan for threats. EventSentry will detect newly added Office documents, scan them, and notify you if any potential threats such as macros or external links are found.
Pre-requisites
To get started, first decide where you would like to monitor Office documents, like a file server. On this host, you will need to install Python 3.x, which is required to run oletools. You can read more about oletools on their github page.
Once you have Python installed, run a command prompt as an administrator and type the following command to install oletools:
py -m pip install -U oletools[full]
This will install oletools and all dependencies onto your host.
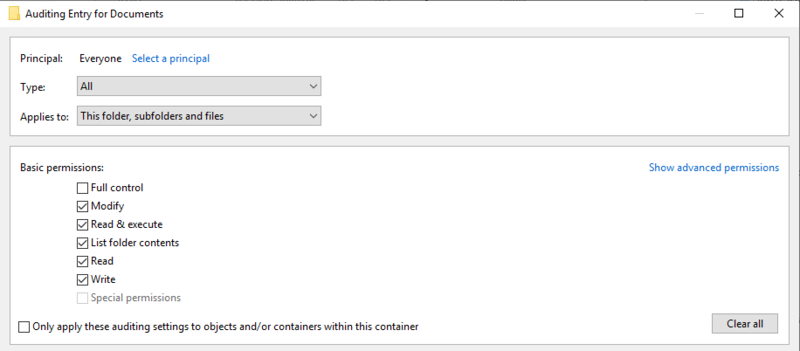
With Python and oletools installed on your host, all that is left is to configure auditing for the folders you want EventSentry to scan. For example, if there is a shared folder on your file server where users often upload Office files you can enable auditing on this folder. To do so, right click the folder, click "Properties," click the "Security" tab, then click "Advanced." In the Auditing tab add the user principal "Everyone," then be sure to at least audit the type "Success" and set the "Applies to" dropdown to at least "Files only." You can choose to audit Successes and Failures (or ALL) and apply to all folders and sub-folders if you wish. You can read more about setting up file auditing from this Microsoft article.
Configuring EventSentry
EventSentry provides a pre-built package that contains all the necessary filters built to scan your Office documents and notify you when potential threats are found. To download it, simply click this link.
This zip file contains the contents of the "configuration" repository from the official EventSentry github. Once you have the zip file downloaded, extract the file titled "es_oleid_4663.reg." You can then install this file your Management Console by clicking "Packages," then click "Import." Import your .reg file then on the left, check the "Office Document Scan" box and import the package. This will add the "Office Document Scan" package to your tree under Packages > Event Logs.
The only thing left to configure is an action that runs the "oleid" executable from oletools.
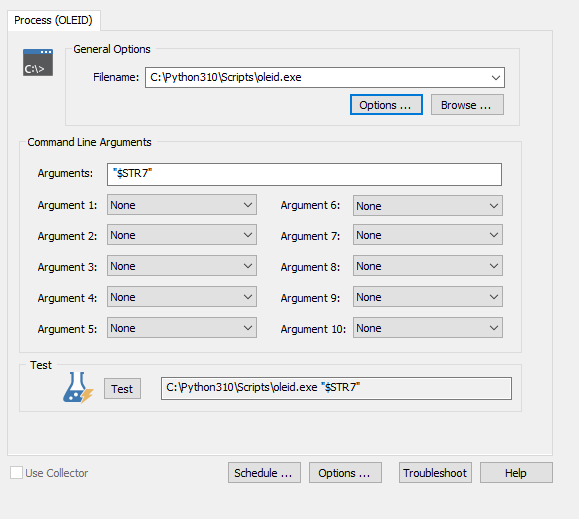
Click Actions > Add > Process to create a Process action. In the "Filename" line you need to point EventSentry to the oleid.exe utility. This file is located in the \Python310\Scripts folder of the Python installation directory on the remote host you installed oletools on by default. So for example, if Python is installed in the program files folder, in the "Filename" line you would need to input: "C:\Program Files\Python\Python310\Scripts\oleid.exe"
In the "Arguments" line, you simply need to input: "$STR7" which is the insertion string from event id 4663. This string contains the full path to the file name being added, and will be passed as an argument to the oleid tool.
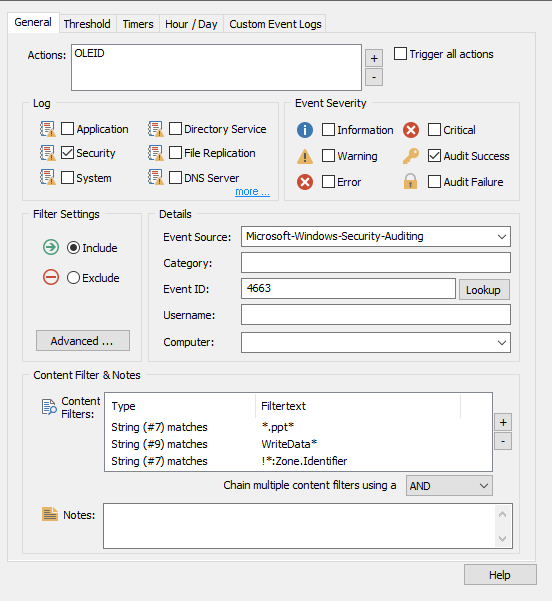
Back in your Office Document Scan package, add your newly created action to the action pane of the "Scan New Document XLS/DOC/PPT/EML" filters. If importing the package automatically added an email or other alert action to these "Scan" filters, remove them to avoid unnecessary spam. The "Email" filters will email you when a risk is detected. You may need to right click the package in the tree, click "Properties," and uncheck the "Override actions of all objects in this package" box.
You can also add or edit the actions of the "Email High Risk/Email Medium Risk" filters to add additional or different email, text, or other actions to alert you when EventSentry finds potential risks.
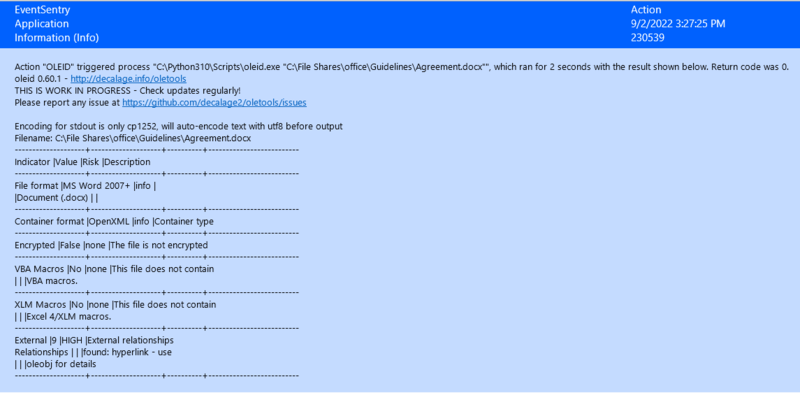
Finally, right click your package in the tree and assign it to the remote host you installed oletools on. Once you save, EventSentry will start scanning new Office files! See below for an example of what a scan result looks like. In this example, a hyperlink was found in the Word document, which prompted a "HIGH" risk result and EventSentry sent an email alert.
Note: For better formatting, the font in EventSentry emails could be customized to a fixed-width font like Courier.