How do I configure an Event Log Filter Threshold?
A standard EventSentry event log filter will forward the configured event to the configured action every time the event occurs. Alternatively, a filter threshold will limit a filter to only perform the configured action if it meets a certain limit.
Agent-Side/Collector-Side
This dropdown in the general settings of the threshold tab determines where this threshold will be counted. Setting this to agent-side means that the threshold will be set per-agent. If for example you set a threshold of 10 in 5 minutes, those 10 events must all occur on one single agent computer in 5 minutes for the threshold to activate. However, if you set this threshold to collector-side this means these events can happen on ANY host and count towards the threshold. This is useful if you want to watch for patterns across your whole network instead of on one agent.
Forwarding events only after the threshold is reached
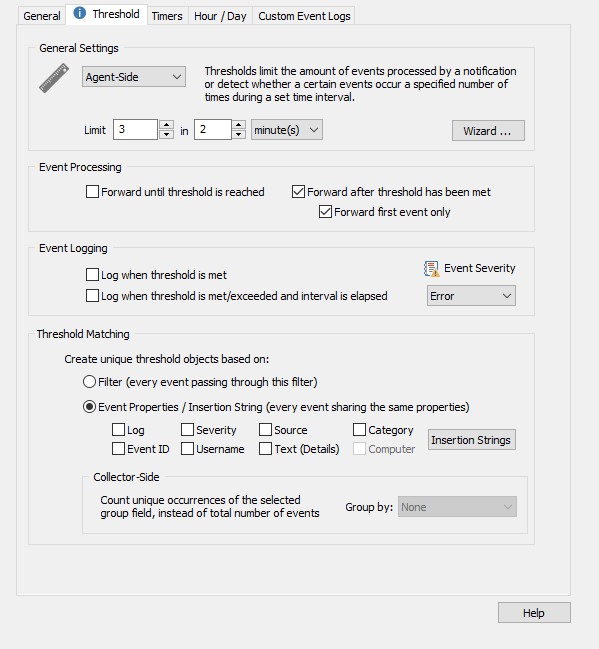
Imagine the common scenario where an employee types a wrong password when logging in. The event generated would be an accident, not a critical security breach. However, if 10+ wrong password attempts were generated in under a few minutes you would want to be alerted. Take note in our example below, under "Event Processing" we have configured the threshold to ONLY forward events AFTER the threshold has been met. In this case, we will only receive an alert when the same event happens 10 times in the span of 5 minutes.
Limiting Redundant Notifications
Filter thresholds can also be used to prevent a filter from flooding an action. An example of this is when Windows writes an event every second to the System log when it discovers a bad block on disk. This is an event you will most likely wish to know about, but you probably do not want to receive 1,000+ emails in 10 minutes. In our example below, the filter will only forward the alert once the threshold has been met AND only send us the first event. This way we will not be spammed with so many emails.
Forwarding events up until the threshold is reached
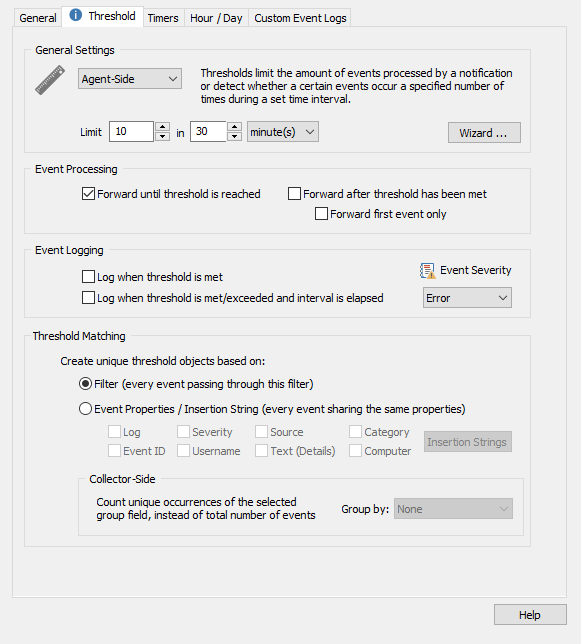
As an alternative to the last scenario where Windows creates thousands of events for a bad sector, say you want to receive the first 10 alerts from this event but no more after that for 30 minutes. In the example below, the filter will perform the configured action up to 10 times in 30 minutes, but no more than that.
Event Logging
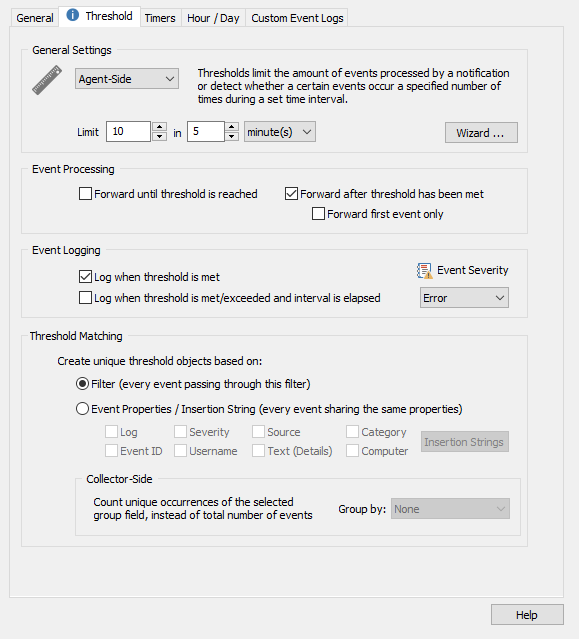
There is also the option to generate events in the Windows Application Event log that indicates when the threshold was met. These events can be used to ensure the threshold is configured correctly and even be sent out as a notification. These are configured in the "Event Logging" section of the threshold tab.
Threshold Matching
If you configure threshold matching settings, then only events that share the matching settings you configure will count towards your threshold. In our first example of a threshold that only activates when a user fails to log on multiple times, you may want to set the threshold match to match account names. That way, the threshold will only activate if there are 10 failed logon attempts from your admin account, for example. You can set an insertion string #2 match, as this will match the account names of the Security Event 4625, an account failed to logon: https://system32.eventsentry.com/security/event/4625