How do I configure Logon/Logoff tracking?
Getting Started
Logon Tracking allows you to track console logons as well as a variety of network logons, both failed and successful. This feature can be found as a tracking item in the EventSentry Management console and requires a database.
Verifying your settings
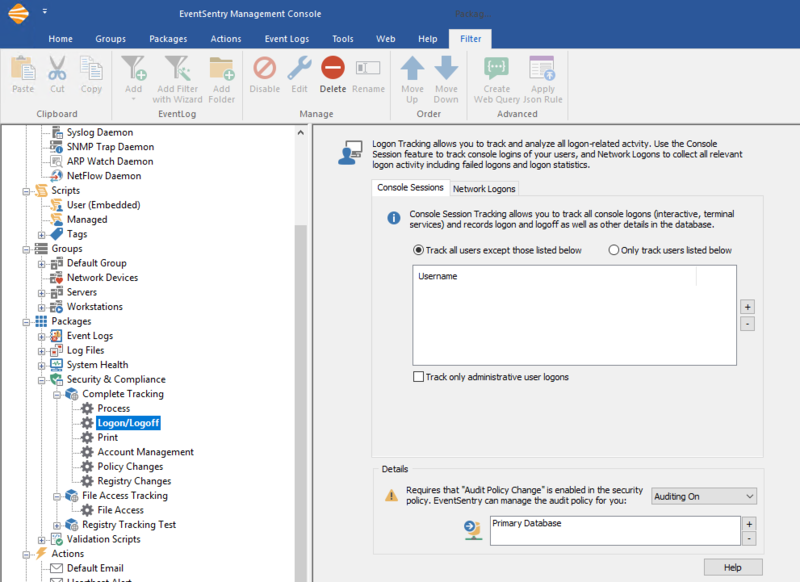
Click the Logon/Logoff item in the Complete Tracking package to see your configuration options.
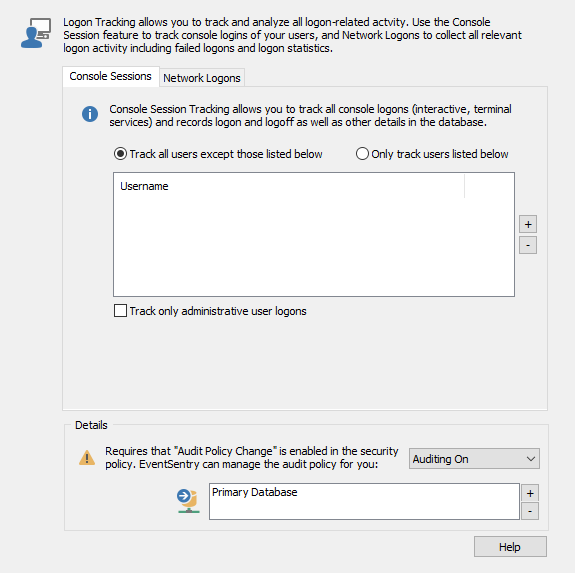
Here you can configure what users you would like to monitor Logon and Logoff events for. For example, you can choose to track all users except for some exceptions. Or you can choose to only track certain users.
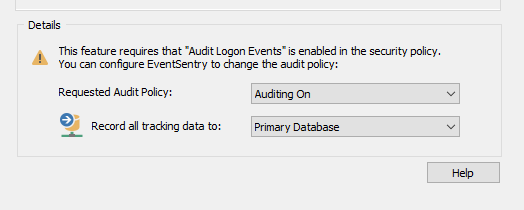
In order for EventSentry to be able to write logon information to the database, the information must be in the event logs in the first place. As a result, you will need to audit Logon and Logoff in the Advanced Audit Policy Configuration of every computer where users log on. If these are not audited then no logon and logoff events will be generated in the security event logs.
We recommend that you configure this option network-wide in a group policy, but if that is not an option then EventSentry can set the Local Policy by setting the "Requested Audit Policy" dropdown to "Auditing On."
Note: Remember that Windows logs all logon/logoff events of console logins (even when they are domain logons) at the actual workstation where users login. As such, you will need to install the EventSentry agents on all workstations where users you wish to track logon.
Viewing with the Web Reports
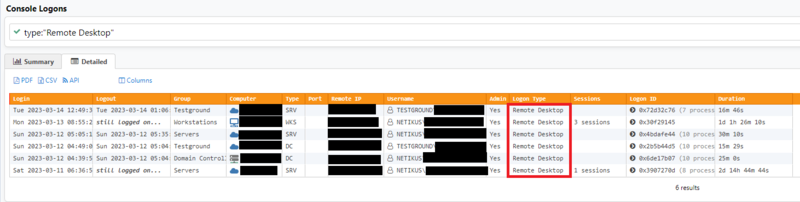
Web Reports allows you to easily view detailed logon information from one central location. On the Console Logons page (Features > Console) you can search for specific users or see who is using Terminal Services.
In the Detailed view we can see when an account logged on through Remote Desktop, for example.
Logon Events by Email
Windows writes the security event ID 4624 for a logon event: https://system32.eventsentry.com/security/event/4624
And the security event ID 4634 for a logoff event: https://system32.eventsentry.com/security/event/4634
As with any event log, EventSentry can set a real-time email alert for Logon and Logoff events. That said, you will need to be sure you set your Event Log filters to be specific to only match the Logon/Logoff events you want alerts for. If your filters are too general (as in they match too many events), then you will probably get more emails than you really want, even on a small network.
Let's say we want an alert that will send an email alert when the user account testadmin logs on through the console (this means by hitting CTRL+ALT+DEL on a computer).
It is always a good idea to stay organized, for this reason we will create a new filter package and call it Logon/Logoff.
Then in our new package, we will add a new filter.
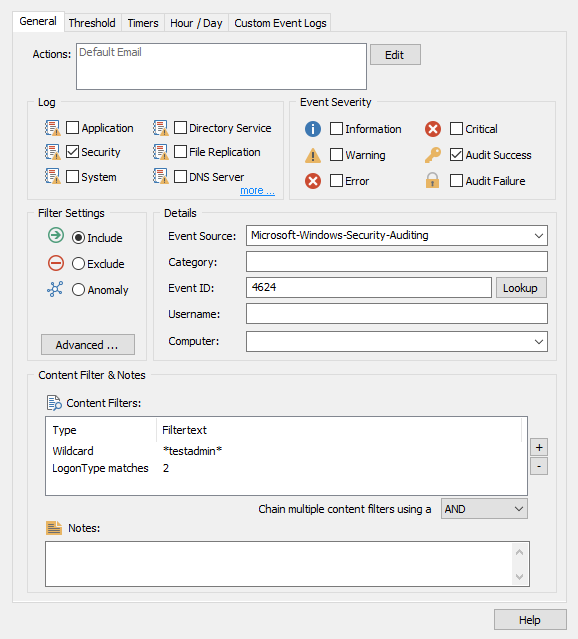
Depending on what you would like to monitor the filter text may vary. In our example, the filter will forward all events with the username testadmin and logon type 2 which is an interactive logon to a computer. You can check the different logon types that Windows logs by opening our site here: https://system32.eventsentry.com/security/event/4624
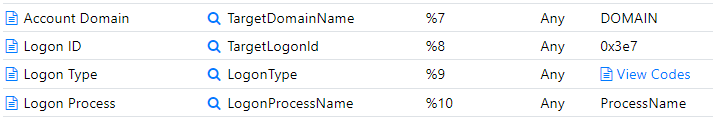
Here you can search for Windows Security Event IDs and see the insertion strings they use. In the case of the 4624 logon event, you can scroll down to String 9 "Logon Type" and click view codes.
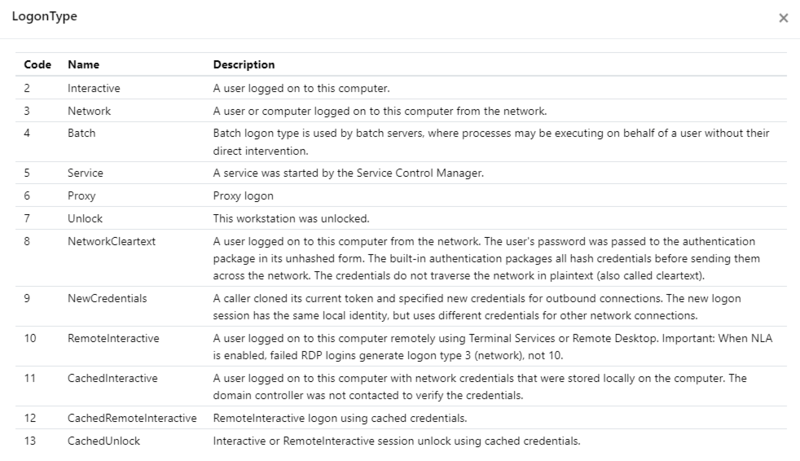
Here you can see the different Logon Type codes. Common logon types are Type 2 (console logon), Type 10 (remote desktop/terminal services logon), and type 11 (cached logon - usually laptops).
Now that the filter is created, you can assign your package to global to monitor all hosts or only to the hosts you wish to monitor Logon/Logoff events for. Once you save from Home > Save you will start receiving those alerts!