How to detect TCP port scans initiated from a windows host
A port scan that is initiated from a monitored host can be detect by monitoring Windows Filtering Platform event id 5156 and applying a threshold filter. Sysmon cannot be used to detect port scans since it only logs successfully established connections.
- Enable auditing to ensure that event id 5156 is logged, see link for instructions.
- Create a package and assign it to the hosts where port scans should be detected.
- Copy the code shown below into the clipboard.
- Click the newly created package in EventSentry and then click the Paste button in the ribbon.
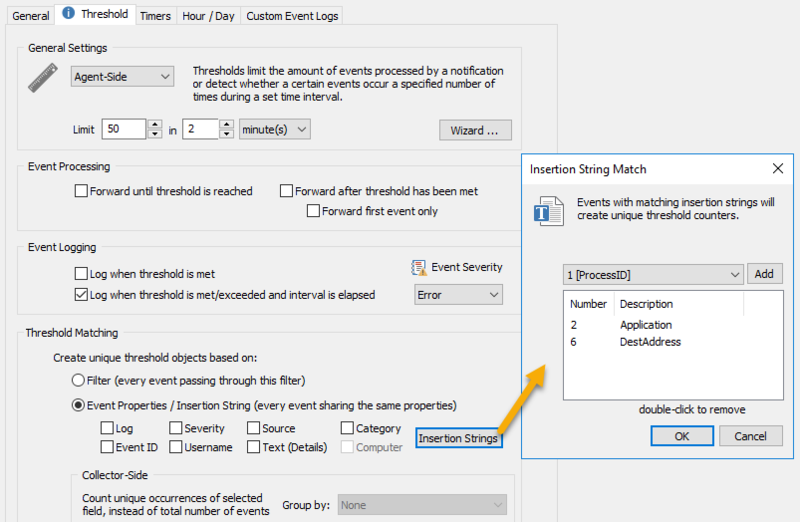
- Click the "Threshold" tab and customize the threshold limit and time frame. This will control how many outgoing connections in which time period will trigger the alert.
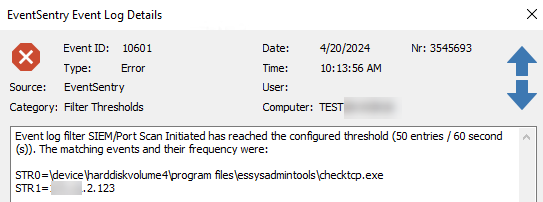
- EventSentry will log event id 10601 when the threshold is met, and this event will contain the name of the process which performed the potential port scan along with the IP address it scanned. If error events are not emailed by default then an additional filter will have to be setup that forward 10601 events.
Important Notes
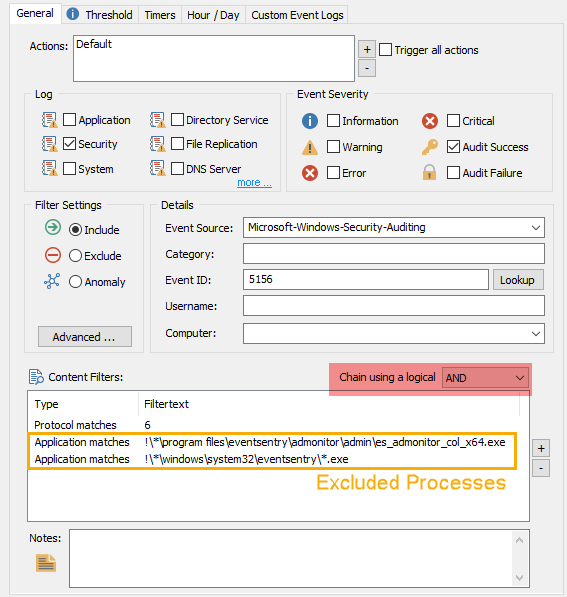
Some processes may open multiple network connections during normal operation, these processes may need to be excluded either with a separate exclude filter, or by adding a content filter as included by default for all EventSentry processes.
EventSentry does not actually analyze the remote ports which are contacted, as such it is possible that a process attempting to connect to the same remote TCP port in fast succession will trigger an alarm as well. Alerts logged by this threshold filter should always be investigated unless they involve a trusted executable.
Storing the actual events which are logged by the Windows Filtering Platform subsystem is generally not recommended due to the high volume of data is likely generated.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 |
{
"type": 0,
"active": 1,
"name": "Port Scan Initiated",
"uuid": "13acfcd4-2999-415d-a5e5-eec8d18933d2",
"version": 1,
"isfolder": 0,
"applyToCollectorSideThresholds": 0,
"requireAck": 0,
"stopProcessing": 0,
"anomalyFiltering": 0,
"logs": [ "SEC" ],"severities": [ "AUDITSUCCESS" ],"source": "Microsoft-Windows-Security-Auditing",
"eventid": "5156",
"chainType": 1,
"textfilters": [ { "insertionString": 7,
"comparisonType": 0,
"text": "6",
"type": 1
},{ "insertionString": 1,
"comparisonType": 0,
"text": "!\\*\\program files\\eventsentry\\admonitor\\admin\\es_admonitor_col_x64.exe",
"type": 1
},{ "insertionString": 1,
"comparisonType": 0,
"text": "!\\*\\windows\\system32\\eventsentry\\*.exe",
"type": 1
}],"threshold": {
"type": 1,
"limit": 50,
"interval": 2,
"intervalScale": 1,
"processBefore": 0,
"processAfter": 0,
"processAfterFirstOnly": 0,
"logImmediate": 0,
"logInterval": 1,
"logSeverity": 2,
"matchType": 0
, "eventProperties" : [ "2", "6" ]
},"bootBehavior": 0
}
|