CJIS Security Policy Compliance
Download Now
Analyze
The EventSentry Web Reports offer a powerful, yet easy to use web interface to review changes on your network.
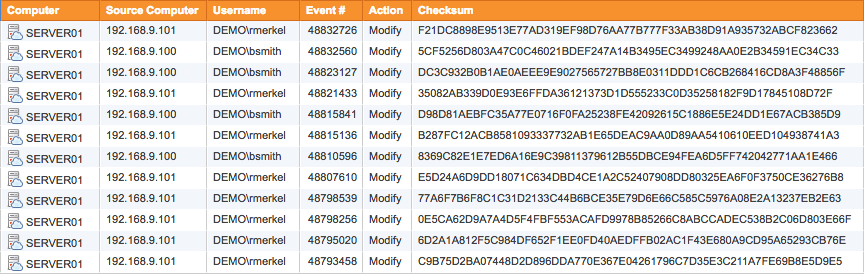
file:vendors.xlsx and action:Modify
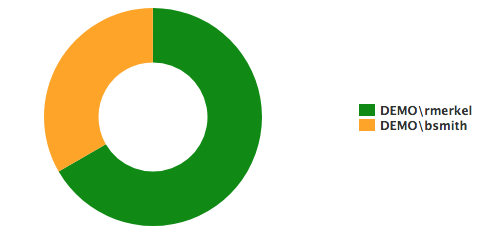
Built-in Reports
EventSentry provides comprehensive out-of-the-box reports to help you meet your NIST 800-171 requirements. Analyze and confirm file access, account changes, and policy changes.
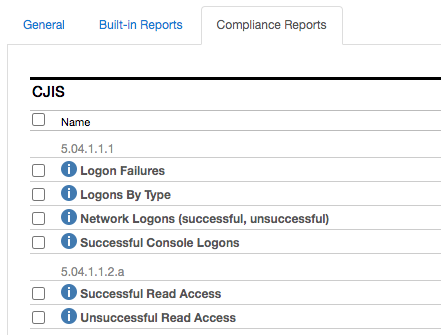
CJIS Security Policy
- A limit of 5 unsuccessful login attempts by a user accessing CJIS
- Event logging various login activities, including password changes
- Weekly audit reviews
- Active account management moderation
- Session lock after 30 minutes of inactivity
- Access restriction based on physical location, job assignment, time of day, and network address
Compliance Tracking Features
Compliance tracking intercepts and normalizes security-related events from the Windows event log, and consolidates them in the EventSentry database. This includes Active Directory Change Reporting (e.g. Account Management Tracking) as well as tracking of user activity (e.g. Logon Tracking). In full, compliance tracking includes the following features:
- Console Logon Tracking
- Process Tracking
- File Access Tracking
- Account Management Tracking
- Policy Change Management Tracking
- Print Tracking