Using Filter Text to match specific events
Using Wildcards (Step 4 of 6)
Wildcards
Wildcard characters allow you to match a group of characters, and support the * and ? characters. Wildcards can be used in any of the follow fields in an event log filter (Regular expression support is also available when matching event log content):
- Event Source
- Category
- Username
- Filter Text
- Computer
Filter with wildcard
Matches string
ipx*
IPXCP
IPXRouterManager
*iptables*proto=??p*dpt=13*
syslog@netikus-router[kern.debug]: kernel: IPTABLES INPUT: IN=ppp0 OUT= MAC= SRC=65.35.223.155 DST=65.41.63.146 LEN=48 TOS=0x00 PREC=0x00 TTL=114 ID=54221 DF PROTO=TCP SPT=1429 DPT=135 WINDOW=64240 RES=0x00 SYN URGP=0
VMnet*
VMnetAdapter
VMnetDHCP
VMnetuserif
*rip*
IPRIP2
IPXRIP
Going back to our example
In the case of monitoring for web service changes we will have to filter based on the text of the message.
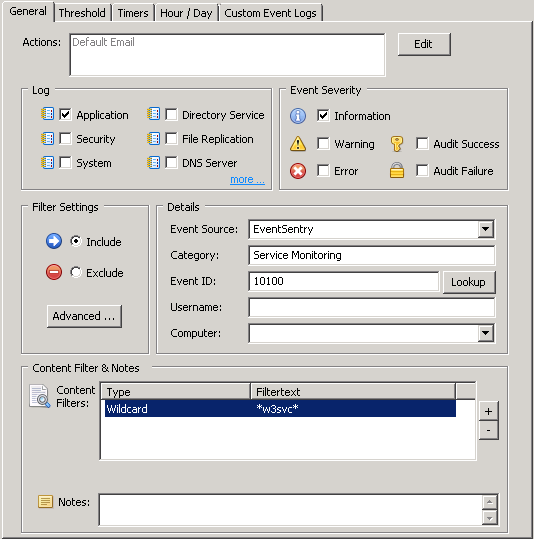
Please note that you will have to click to the + to add Filter Text
By simply adding a wildcard before and after the text we are looking for, we are excluding every event that occurs that does not contain that message text.
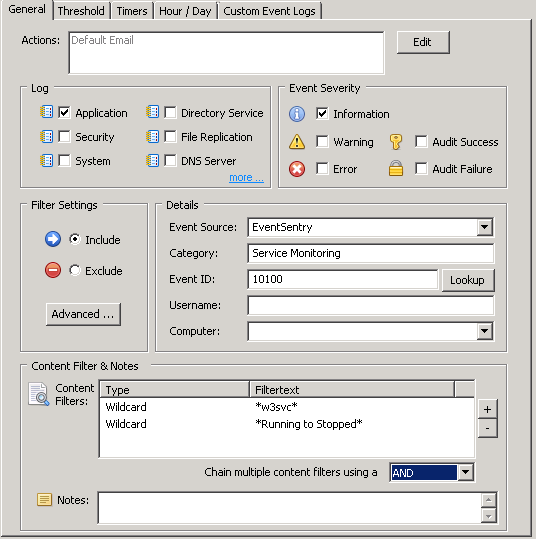
Even more specific
We can go even further and only receive an email if someone stops the services.
- Updated on: 2015-01-21
- Skill Level: Advanced
- LEFT/RIGHT arrow keys for navigation